Most people don’t remember PowerPoint slides and PDFs about company policies. They remember what they do. That’s why gamification works so well for staff training, especially in cyber security. It turns “watch and forget” into “play and learn.”
Lets take an example. Imagine an escape room style point-and-click game that challenges employees to spot and solve potential security threats like phishing emails, or data vulnerability in the office. A timer counts down from 20 minutes at the top of the screen, and they can accept hints in exchange for a time penalty. Lets explore why this works, and how to do it well...

What gamification really means
- Real actions, not passive watching: Spot the phishing message, choose whether to trust a voicemail, classify a document. Make the call and see the consequence.
- Stakes and momentum: Timers, hints, and progress unlocks keep people moving without overwhelming them.
- Social pull: Team play and leaderboards create friendly pressure and shared responsibility.
- Clear feedback: Scores and puzzle-level data show what clicked and what needs a refresher.
Why it sticks
- It mimics everyday work: Email, SMS, social posts, CCTV, passwords; the same channels people use daily.
- It’s emotional: A ticking clock and a story give choices weight, which boosts memory.
- It respects time: Short, focused challenges beat an hour-long webinar.
- It’s measurable: You can track completion, strengths, and gaps to tailor follow-ups.
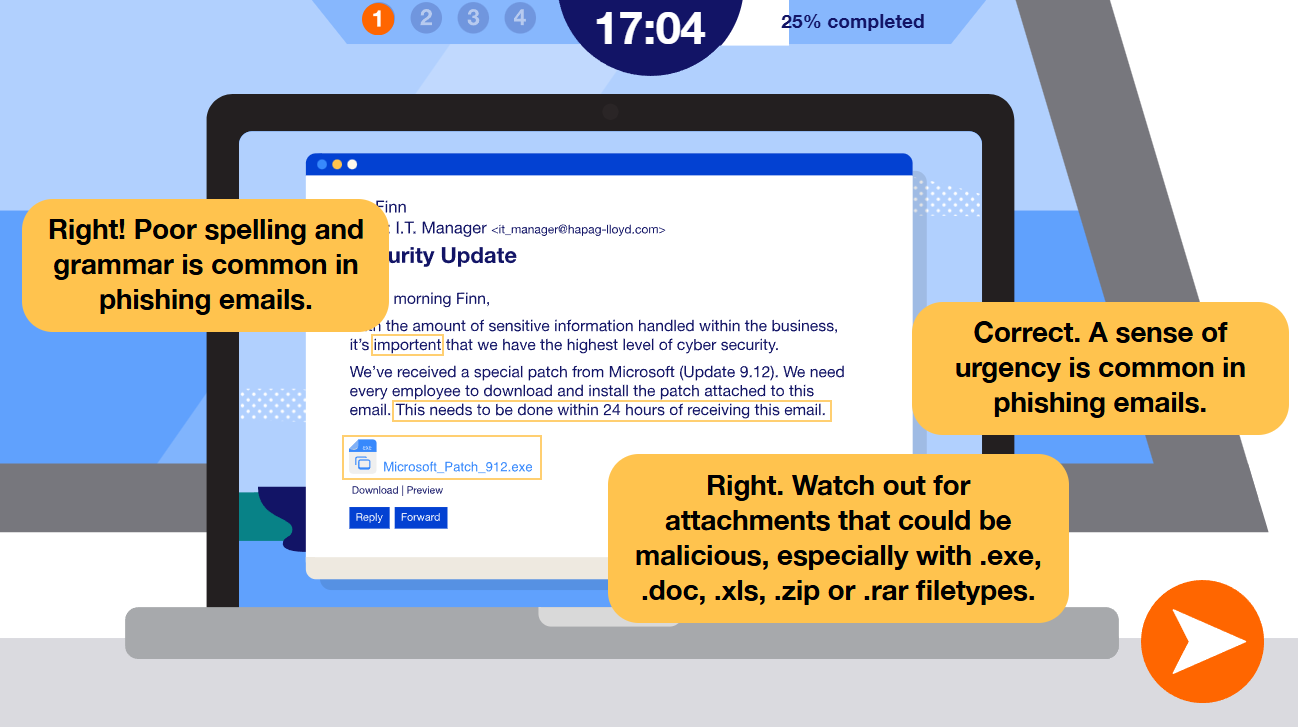
How to design it well
- Start with behaviours, not trivia: Build challenges around the exact actions you want. Reporting suspicious messages, using MFA correctly, handling data safely.
- Keep the rules simple: One clear goal per puzzle. Teach through doing, not through long instructions.
- Balance pressure and fairness: Timers should encourage, not punish. Use hints that cost time to keep momentum.
- Make it collaborative: Let teams nominate a leader and solve together. Great for culture and learning.
- Close the loop: After each challenge, give a quick “why this matters” so lessons transfer to the day job.
- Measure what matters: Track not just scores, but which threats people miss, and use that to plan your next campaign.
Where it fits in a training programme
- Onboarding: A guided “first mission” that covers the basics in 15 - 20 minutes.
- Quarterly refreshers: Rotate new puzzles for new threats (MFA fatigue, QR codes, deepfake voicemails).
- Campaign weeks: Launch a themed game to rally the whole business.
- Compliance: Use analytics to evidence coverage, improvement, and where to focus.
A few pitfalls to avoid
- Over-gamifying: Flashy mechanics can distract from the learning. Keep it purposeful.
- One-and-done: The impact fades if you don’t follow up. Treat it like a series, not a single event.
- No data plan: If you’re not using the performance data, you’re leaving value on the table.
How Spinbox has applied this (quick examples)
- Virtual escape rooms for global teams: We helped Ahold Delhaize, and others turn cyber training into interactive games using Angular. Think phishing flags, voicemail trust decisions, safe-cracking logic, and CCTV hazard spotting; played solo or in teams with a leader.
- A central arcade to run it all: We built the Living Data Arcade to host games, handle secure sign-in (Azure AD), and power leaderboards and reporting via Umbraco.
- Proven engagement: After launch, they saw a 20% uplift in participation and record week-one play for a major release.
If you’re considering gamified training
- Start small: One focused challenge that targets a common risk.
- Pilot with a few teams: Watch where they stall and refine the puzzles.
- Ship regularly: New chapters or themes keep it fresh and relevant.
- Tell the story: Tie each release to current threats or incidents to make it feel timely.
Want help turning your security training into something people love to play and actually learn from? We can design the game mechanics, puzzles, and platform to fit your risks, culture and tech stack.